Knowledge of network configuration and administration is an (incredibly- still) underrated, underappreciated and immensely powerful tool for any IT professional to possess.
One area of computer networking that should be more well-understood by software developers is the configuration of subnetworks via subnet masks. A subnet mask (ie. 255.255.255.0) is simply a way of re-purposing an IP Address by segmenting it into network and host portions.
An IPv4 address consists of 4 bytes (32 bits) of data. Each of those bytes contain 8 bits known as "octets". In a 255.255.255.0 subnet mask- all but the last octet is being used for the network ID portion of the IP address and so are ignored.
At this point we could get into the logical ANDing of IP address bits and subnet mask bits but just be aware that the masking bits allow for the network portion of the IP address to be separated from the host portion- that is they key purpose of subnetting and the subnet mask.
The subnet mask is designed to denote the number of bits in an IP address (ie. 10.9.1.14) that form the network portion (10.9.1) vs. the host portion (.14).
In this way, IPs can be used in ways they were not originally designed- but that are altogether needed for proper organization of something that has grown as seemingly unwieldy as IP networks of "the Internet" (publically accessible networks of subnetworks). With a little reference knowledge you can understand even the trickiest of subnet configurations.
But wait- there is (lots) more...
The example above illustrates only a very basic subnetting situation.
Where things get tricky is when a subnet mask ends not at the end of an entire octet, but just before the start of the host portion of the IP- in the same octet (ie. 255.255.128.0). In more complex network configuration scenarios it is helpful to refer to a subnet configuration reference sheet like the following to identify the subnet and/or subnet mask information you are looking for:
Below are the 7 common pieces of information that you will need to know when analyzing subnet configurations:
Network ID: First available IP address in the subnet.
Broadcast IP: Last available address in the subnet.
First Host IP: Network ID + 1
Last Host IP: Broadcast IP - 1
Next Network: Broadcast + 1
# of IP Addresses: Number of IP addresses in the subnet range (subtract 2 to find the number of "usable" device IP addresses) - refer to the Subnet Mask Reference Sheet
IP Points to remember:
References:
https://www.youtube.com/watch?v=s_Ntt6eTn94&ab_channel=PowerCertAnimatedVideos
https://www.youtube.com/watch?v=BWZ-MHIhqjM
http://www.subnet-calculator.com/
https://www.pcwdld.com/subnet-mask-cheat-sheet-guide
All subnet masking schemes, the mask bits in binary, available number of hosts. A "/24" is common for small LAN subnets.
An IPv4 address consists of 4 bytes (32 bits) of data. Each of those bytes contain 8 bits known as "octets". In a 255.255.255.0 subnet mask- all but the last octet is being used for the network ID portion of the IP address and so are ignored.
At this point we could get into the logical ANDing of IP address bits and subnet mask bits but just be aware that the masking bits allow for the network portion of the IP address to be separated from the host portion- that is they key purpose of subnetting and the subnet mask.
The breakdown of a Class B IPv4 address
In this way, IPs can be used in ways they were not originally designed- but that are altogether needed for proper organization of something that has grown as seemingly unwieldy as IP networks of "the Internet" (publically accessible networks of subnetworks). With a little reference knowledge you can understand even the trickiest of subnet configurations.
But wait- there is (lots) more...
The example above illustrates only a very basic subnetting situation.
Where things get tricky is when a subnet mask ends not at the end of an entire octet, but just before the start of the host portion of the IP- in the same octet (ie. 255.255.128.0). In more complex network configuration scenarios it is helpful to refer to a subnet configuration reference sheet like the following to identify the subnet and/or subnet mask information you are looking for:
Describing the nature of a /29 subnet solely from knowing the IP address (10.1.1.37) of one of its hosts and that it is a /29 subnet.
Below are the 7 common pieces of information that you will need to know when analyzing subnet configurations:
Network ID: First available IP address in the subnet.
Broadcast IP: Last available address in the subnet.
First Host IP: Network ID + 1
Last Host IP: Broadcast IP - 1
Next Network: Broadcast + 1
# of IP Addresses: Number of IP addresses in the subnet range (subtract 2 to find the number of "usable" device IP addresses) - refer to the Subnet Mask Reference Sheet
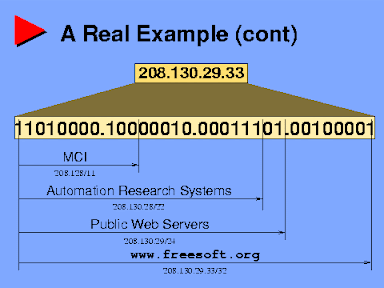
This enlightening example shows how MCI uses 11 bits of mask, Automation Research Systems 22 bits, ARS 24 bits, freesoft.org 32 bits- all on the same IP address; you can see the subnet hierarchy as MCI controls the entire 208.128.0.0/11 network
Online CIDR Calculator showing MCI subnet breakdown which includes the other 3 subnets shown
IP Points to remember:
- IP octets (base 10 representation) are 0-inclusive so only ever max of .255 in any given octet.
- Subnet Mask is a 32-bit number that indicates how many bits of an IP address are used to indicate the network portion vs. host portion and is a way to subdivide networks for organization, security and manageability.
- The first two available host addresses are network (generally .0), then router (generally .1) and the last available host address (generally .255) is used as the subnet's broadcast address- note these example octets are small LAN defaults/generalities and likely will not apply to a complex subnet.
- Class A (0-127) uses 8 bits for the network portion of the IP address, leaving 24 bits for host IDs
- Class B (128-191) uses 16 bits for the network portion of the IP address, leaving 16 bits for host IDs
- Class C (192-223) uses 24 bits for the network portion of the IP address, leaving 8 bits for host IDs
- CIDR is the acronym for Classless Inter-domain Routing. It (/26, /24, etc.) is just the number of IP address bits used by the subnet mask (255.255.255.0 = /24 or 24 bits of mask, .255.255.255.192 = /26 or 26 bits of mask).
- When sorting through IP ranges to determine which range a particular subnetwork group is in, use these time saving tricks recommended by PracticalNetworking:
- (1) multiply group size by 10 as a (*10) multiple of the group size will be reached
- (2) if multiplying group size by 10 goes beyond the IP address for which you are trying to find the subnetwork range, remember that "every group size will land on 128 eventually"- so you can use that for a starting basis as well.
- (3) every group size lands on the subnet value of the selected subnet and every subnet to the left of it (ie. for a /27 subnet or ".224" subnet mask- .224, .192 and .128 will all match the start of a group)
References:
https://www.youtube.com/watch?v=s_Ntt6eTn94&ab_channel=PowerCertAnimatedVideos
https://www.youtube.com/watch?v=BWZ-MHIhqjM
http://www.subnet-calculator.com/
https://www.pcwdld.com/subnet-mask-cheat-sheet-guide