Man in the Middle: "an attack where the attacker secretly relays and possibly alters the communications between two parties who believe they are directly communicating with each other."-Wkipedia.
A MITM or MTM attack does not happen at the source or destination but rather along the route between them. To prevent this type of attack one must ensure the integrity of their network. This includes enabling only the latest recommended security protocols, ensuring SSL cannot be impersonated, and general configuration of network firewalls and routing equipment to ensure no unauthorized user can ever connect to your router or any other interception point.
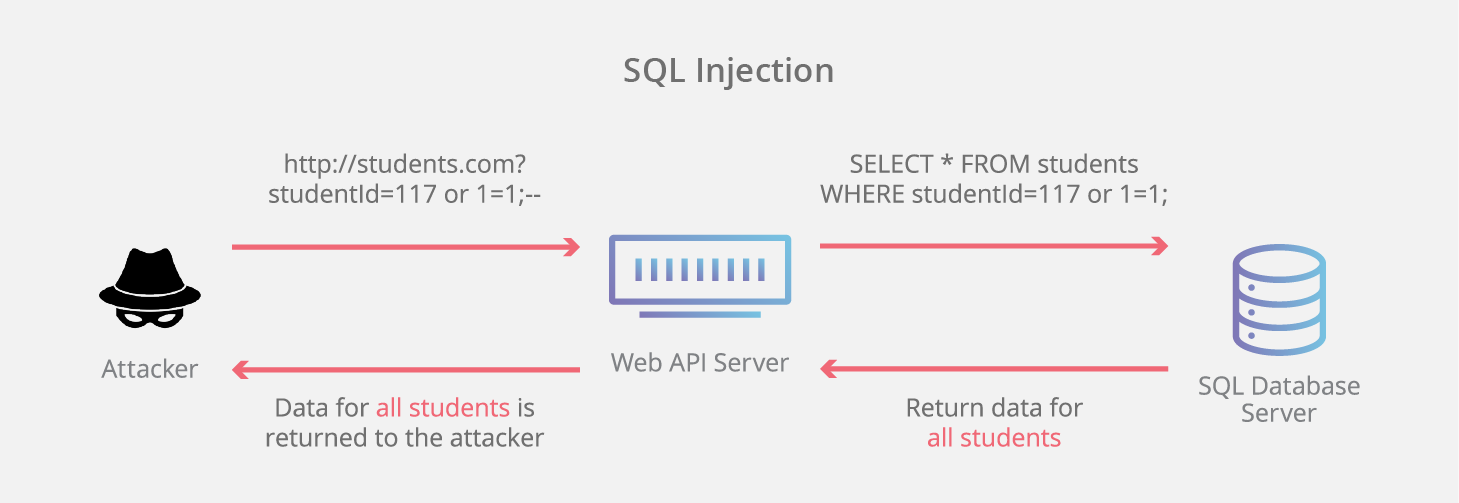
SQL Injection: "An SQL injection is a computer attack in which malicious code is embedded in a poorly-designed application and then passed to the backend database. The malicious data then produces database query results or actions that should never have been executed." -Techopedia.com
Cross-site Scripting (XSS): "XSS enables attackers to inject client-side scripts into web pages viewed by other users." -Wikipedia
For a basic example, if UserA is logged into some secure that is authenticating each UserA HttpRequest via a key that UserX can obtain- (perhaps by successfully MITM'ing)- UserX can then impersonate User A by using UserA's authentication key to craft HttpRequests containing malicious scripts that run automatically on User A's browser.
Buffer Overflow Attack:

Buffer Overflow attacks cause a memory buffer boundary (stack or heap) to be exceeded and memory pointers to be overwritten to point to attackers own malicious functions instead of the normal user, machine or OS instructions.
Intrusion detection systems can be used to mitigate this type of attack by alerting Network Administrators if any irregular/bad actor is on the network. Some well-known buffer overflow attacks: https://www.cypressdatadefense.com/education-training/buffer-overflow-attacks-need-know/
Rootkit Deployment: "A rootkit is a clandestine computer program designed to provide continued privileged access to a computer while actively hiding its presence." -Veracode.com
The unique feature of rootkits is their design to be undetectable. In Windows systems for instance, rootkits will override Win32 API methods that the OS uses to verify the integrity and authorization of certain method calls, etc. In this way, rootkits can allow a malicious program to run in the background, undetected by most normal system checks. Sysinternals' RootKitRevealer can show you if your machine is affected by any rootkit-based malware.

The following are some of the more well-known Exploits:
StuxNet: Uncovered in 2010, this severely malicious virus spread through Windows USB "Autorun" feature and mostly affected an Iranian nuclear enrichment plant. StuxNet was a self-propagating worm hidden via root level masking. The machine operators had no forewarning that StuxNet was installed and configured to ruin several centrifuges. StuxNet was developed jointly by US and Israeli cyber actors. Shockingly, the Iran centrifuge destruction was "just a test" of StuxNet's power. It successfully stalled Iran's nuclear enrichment program for up to several years according to NY Times researchers: https://www.nytimes.com/2011/01/16/world/middleeast/16stuxnet.html
WannaCry: "The WannaCry ransomware attack was a May 2017 worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency." - Wikipedia
WannaCry affected a number of targets (and successfully extorted a number of ransoms) including Britain's National Health Institute.
Sony Music: Sony's privates network was compromised by a group calling themselves "Guardians of Peace". The attack apparently happened simply from one of the attackers obtaining admin credentials through email phishing. Embarrassing internal email correspondence and future film material was leaked to the public. Ultimately, North Korean Park Jing Hyok has been charged for the Sony attack as well as the WannaCry ransom attack: https://www.pbs.org/newshour/nation/north-korean-programmer-charged-in-sony-hack-wannacry-attack
Spectre: In 2018 this hardware-based attack method altered the way microprocessors perform a basic branch speculation function which leads to side effects that include revelations of what was in the process instruction, private data, etc. Although this attack is not remotely exploitable, it is likely to go undetected unless systems are maintained and secured diligently.
Cybersecurity Organizations and Resources:
OWASP Free and Open Security Community
Offensive Security
Microsoft Security
Android Security
Linux Security
A MITM or MTM attack does not happen at the source or destination but rather along the route between them. To prevent this type of attack one must ensure the integrity of their network. This includes enabling only the latest recommended security protocols, ensuring SSL cannot be impersonated, and general configuration of network firewalls and routing equipment to ensure no unauthorized user can ever connect to your router or any other interception point.
SQL Injection: "An SQL injection is a computer attack in which malicious code is embedded in a poorly-designed application and then passed to the backend database. The malicious data then produces database query results or actions that should never have been executed." -Techopedia.com

Cross-site Scripting (XSS): "XSS enables attackers to inject client-side scripts into web pages viewed by other users." -Wikipedia
For a basic example, if UserA is logged into some secure that is authenticating each UserA HttpRequest via a key that UserX can obtain- (perhaps by successfully MITM'ing)- UserX can then impersonate User A by using UserA's authentication key to craft HttpRequests containing malicious scripts that run automatically on User A's browser.
Buffer Overflow Attack:
Buffer Overflow attacks cause a memory buffer boundary (stack or heap) to be exceeded and memory pointers to be overwritten to point to attackers own malicious functions instead of the normal user, machine or OS instructions.
Intrusion detection systems can be used to mitigate this type of attack by alerting Network Administrators if any irregular/bad actor is on the network. Some well-known buffer overflow attacks: https://www.cypressdatadefense.com/education-training/buffer-overflow-attacks-need-know/
Rootkit Deployment: "A rootkit is a clandestine computer program designed to provide continued privileged access to a computer while actively hiding its presence." -Veracode.com
The unique feature of rootkits is their design to be undetectable. In Windows systems for instance, rootkits will override Win32 API methods that the OS uses to verify the integrity and authorization of certain method calls, etc. In this way, rootkits can allow a malicious program to run in the background, undetected by most normal system checks. Sysinternals' RootKitRevealer can show you if your machine is affected by any rootkit-based malware.

Sony Music infamously used rootkits: https://blogs.technet.microsoft.com/markrussinovich/2005/10/31/sony-rootkits-and-digital-rights-management-gone-too-far/
The following are some of the more well-known Exploits:
StuxNet: Uncovered in 2010, this severely malicious virus spread through Windows USB "Autorun" feature and mostly affected an Iranian nuclear enrichment plant. StuxNet was a self-propagating worm hidden via root level masking. The machine operators had no forewarning that StuxNet was installed and configured to ruin several centrifuges. StuxNet was developed jointly by US and Israeli cyber actors. Shockingly, the Iran centrifuge destruction was "just a test" of StuxNet's power. It successfully stalled Iran's nuclear enrichment program for up to several years according to NY Times researchers: https://www.nytimes.com/2011/01/16/world/middleeast/16stuxnet.html
WannaCry: "The WannaCry ransomware attack was a May 2017 worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency." - Wikipedia
WannaCry affected a number of targets (and successfully extorted a number of ransoms) including Britain's National Health Institute.
Sony Music: Sony's privates network was compromised by a group calling themselves "Guardians of Peace". The attack apparently happened simply from one of the attackers obtaining admin credentials through email phishing. Embarrassing internal email correspondence and future film material was leaked to the public. Ultimately, North Korean Park Jing Hyok has been charged for the Sony attack as well as the WannaCry ransom attack: https://www.pbs.org/newshour/nation/north-korean-programmer-charged-in-sony-hack-wannacry-attack
Spectre: In 2018 this hardware-based attack method altered the way microprocessors perform a basic branch speculation function which leads to side effects that include revelations of what was in the process instruction, private data, etc. Although this attack is not remotely exploitable, it is likely to go undetected unless systems are maintained and secured diligently.
Cybersecurity Organizations and Resources:
OWASP Free and Open Security Community
Offensive Security
Microsoft Security
Android Security
Linux Security


No comments:
Post a Comment